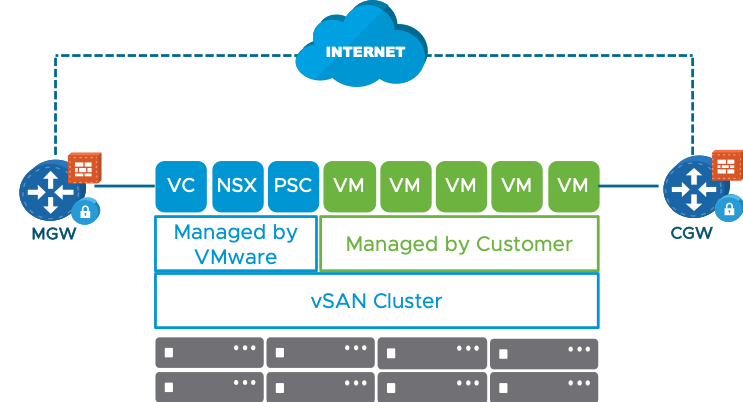
The Management Domain is protected by a Management Gateway [MGW], which is an NSX Edge Security gateway that provides north-south network connectivity for the vCenter Server and NSX Manager running in the SDDC.
The Internet-facing IP address is automatically assigned from the pool of AWS public IP addresses when the SDDC is created. The management logical network internal to your SDDC is assigned the CIDR block 10.0.0.0/16 by default. When you create your SDDC, you can assign a different address block to prevent address conflicts with other environments that you connect to your SDDC.
The Compute Domain is protected by a Compute Gateway [CGW]. The CGW provides north-south network connectivity for virtual machines running in the SDDC. VMware Cloud on AWS creates a default logical network to provide networking for these VMs. You can create additional logical networks in the VMC console and attach these VMs to these networks via vCenter.
The CGW and MGW provides firewall capabilities.
Edge Firewall Rules
By default, the firewall for the compute gateway is set to deny all uplink interfaces which include, internet, Amazon Direct Connect, and Amazon VPC interface and VPN tunnel interface traffic. Add additional firewall rules to allow workload traffic as needed.
Firewall rules control what traffic is allowed based upon the following criteria:
- Source
- Destination
- Services (TCP/UDP ports)
- Action (Allow, Drop or Reject)
- Logging
For the Management Gateway, by default, the firewall is set to deny all inbound and outbound traffic. Add additional firewall rules to allow traffic as needed.
For the Compute Gateway, we can apply the firewalling on different interfaces:
- Customer Native AWS VPC Interface
- Direct Connect Interface
- Internet Interface
- VPN Tunnel Interface
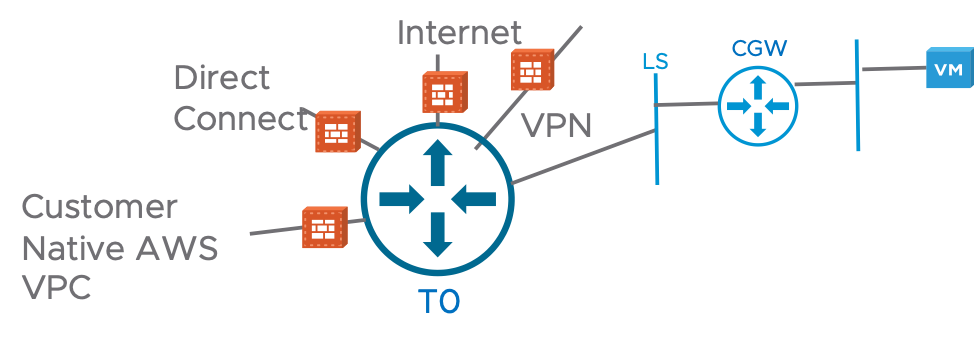
You will see in the “Apply to” Firewall Rules the uplinks where you can apply the rules:


14 thoughts on “Edge Firewalls”